
Bloodhound: Two Sides of the Security Coin for Red and Blue Teams
Are you aware of all permissions applied to your AD groups?
Do you know if any of these permissions could allow an attacker to escalate privileges?
Do you know all the paths an attacker could take to become a Domain Admin within your network?
No? Well, Bloodhound can help your security team visualise the whole domain and look at its security through an attacker’s eyes!
Intro to Bloodhound
Bloodhound is an open-source tool that has been designed to present relationships and communication paths within an Active Directory (AD) environment. The tool allows for the automation of finding highly complex and hidden attack paths , allowing an adversary to work out their next escalation moves or for a defender to shut down and monitor any of these avenues of attack. The attack paths are represented in a graphical interface to make the information easily digestible to any user. These attack paths range from potential privilege escalation paths, lateral movement across networks or complete domain takeover.
In fact, the Bloodhound tool is so powerful that Microsoft integrated its version of Bloodhound within the Advanced Threat Protection Solution! The tool is open-source and very easy to configure, making it highly available. Installation steps can be found on the Github page here:
https://Bloodhound.readthedocs.io/en/latest/installation/linux.html
https://github.com/BloodhoundAD/Bloodhound
All of this makes the tool perfect for a red-team simulation, blue-team review or a purple-team event. This blog will go into how it can be utilised for all three of these scenarios.
This guide uses a Sharphound scan of TryHackMe’s Exploiting AD Network as an example. Sharphound is part of the bloodhound tool, and it is a program that needs to be run on the target network. It will then gather information about the domain. This information then needs to be extracted from the attacker’s machine and uploaded to Bloodhound, which will then display the extracted information in a graphical view.
Red-Team Perspective: Planning Attacks with Bloodhound
To utilise Bloodhound as a red-teamer/adversary, an initial compromise must have already occurred within the target domain. This could be via phishing, brute-force/password spraying or through a vulnerable software/service.
Once access has been gained, the attacker will need to upload, run, and export the output of the enumeration part of the Bloodhound tool called Sharphound.
Sharphound will need to be installed and compiled from Github, or a pre-compiled version can be downloaded from the Bloodhound Github. (I would always suggest compiling it yourself, as it is always better to be cautious when dealing with downloadable executables).
The Sharphound version will need to match the Bloodhound version. Otherwise, the output files may not be compatible with Bloodhound.
Once Sharphound has been compiled and is on a compromised machine within the AD network, the red-team/adversary will need to run the tool to collect information about the domain.
Sharphound has multiple flags that will customise the scope and output depending on the requirements. Some flags help limit the bandwidth of the tool to avoid detection by the blue team.
Once Sharphound is successfully executed on the domain, a file will be created with a name resembling <DATE>_Bloodhound.zip. We need to extract this file and get it onto our host machine. We can use a Python web server, SCP or any other method.
Once the zip file is on our attack machine, we can upload it to Bloodhound and start to look for potential avenues for privilege escalation or lateral movement. The Bloodhound Graphical User Interface (GUI) comes with many interesting and powerful pre-set queries that can help identify these avenues.
We can access these queries by selecting the burger icon at the top left and clicking across through Database Info, Node Info, and Analysis. The Node Info and Analysis hold and display some vital information and queries when trying to plot attack paths.
The Node Info hosts information and stats about the selected node (group/user/workstation/server). The Analysis tab contains the pre-defined queries that massively aid in the enumeration steps.
The below image displays the information that can be found within the Node Info and Analysis menus. In this example, the Node Info shows that there are 7 Reachable High-Value Targets from the Domain Admins group, the description of the group, the groups DomainID, ObjectID, DistinguishedName & when the group was created. The Analysis tab hosts a wide range of pre-built queries that can be executed to find potential escalation or lateral movement points.
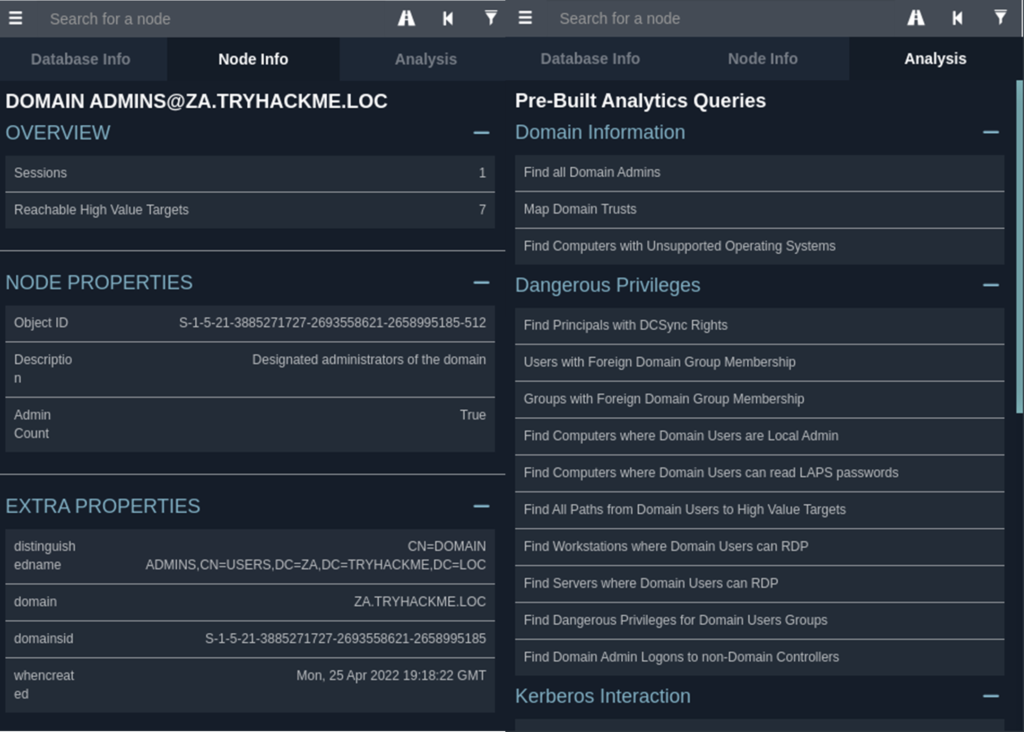
Node Info and Analysis Tabs
Whilst these pre-set queries can be very beneficial in initial enumeration, they can become quite messy to work through, especially when working within a large network. For example, the “Find Shortest Paths to Domain Admins” query will plot a path from multiple starting points, indicating the movement steps to the Domain Admin group.
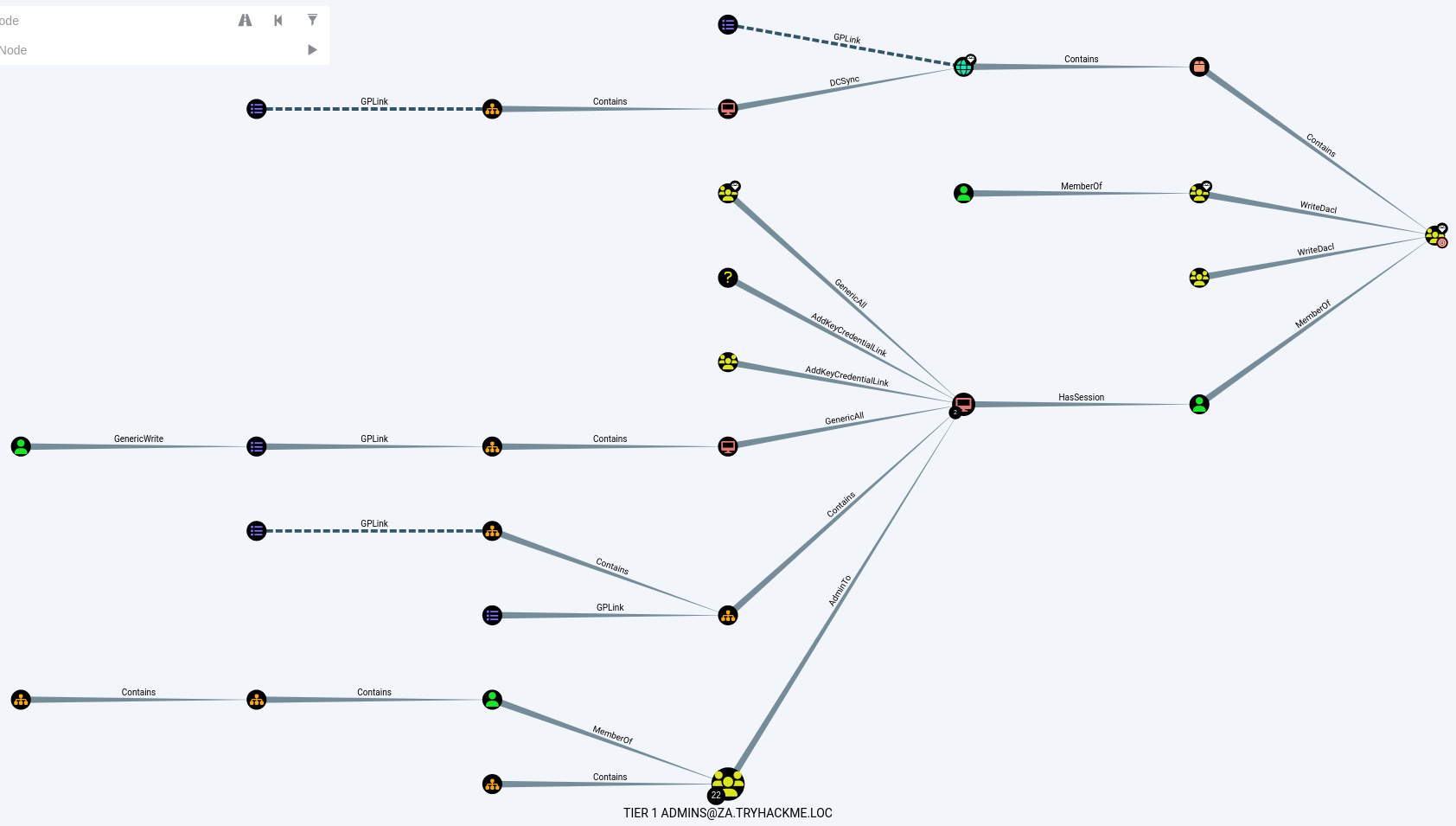
“Find Shortest Paths to Domain Admins” query
This is where the roadmap aspect of Bloodhound becomes critical. If user enumeration has been completed, then the red team will know the names of Administrator groups and low-level accounts that they could potentially compromise. Selecting the road icon opposite the burger, a user is able to list an account or group to start with and then a target account. If possible, Bloodhound will plot an escalation path between the two accounts.
In this example, the red-team has found that they can compromise the SVCSERVMAN account and want to gain access to the Tier 1 Admins group. By selecting the road icon next to the burger and inputting the user and group, Bloodhound will plot a path for potential compromise.
The image below shows the escalation path from the SVCSERVMAN account all the way to the Tier 1 ADMINS group and how each step can be completed.
The path from SVCSERVMAN to Tier 1 ADMINS:
- SVCSERVMAN -> Generic Write -> Management Server Pushes
- Management Server Pushes -> GPLink -> Management Server
- Management Server -> Contains -> THMServer2
- THMServer2 -> GenericAll -> THMServer1
- THMServer1 -> Has Session -> Administrator
- Administrator -> MemberOf -> ADMINISTRATORS
- ADMINISTRATORS -> GenericWrite -> Tier 1 ADMINS
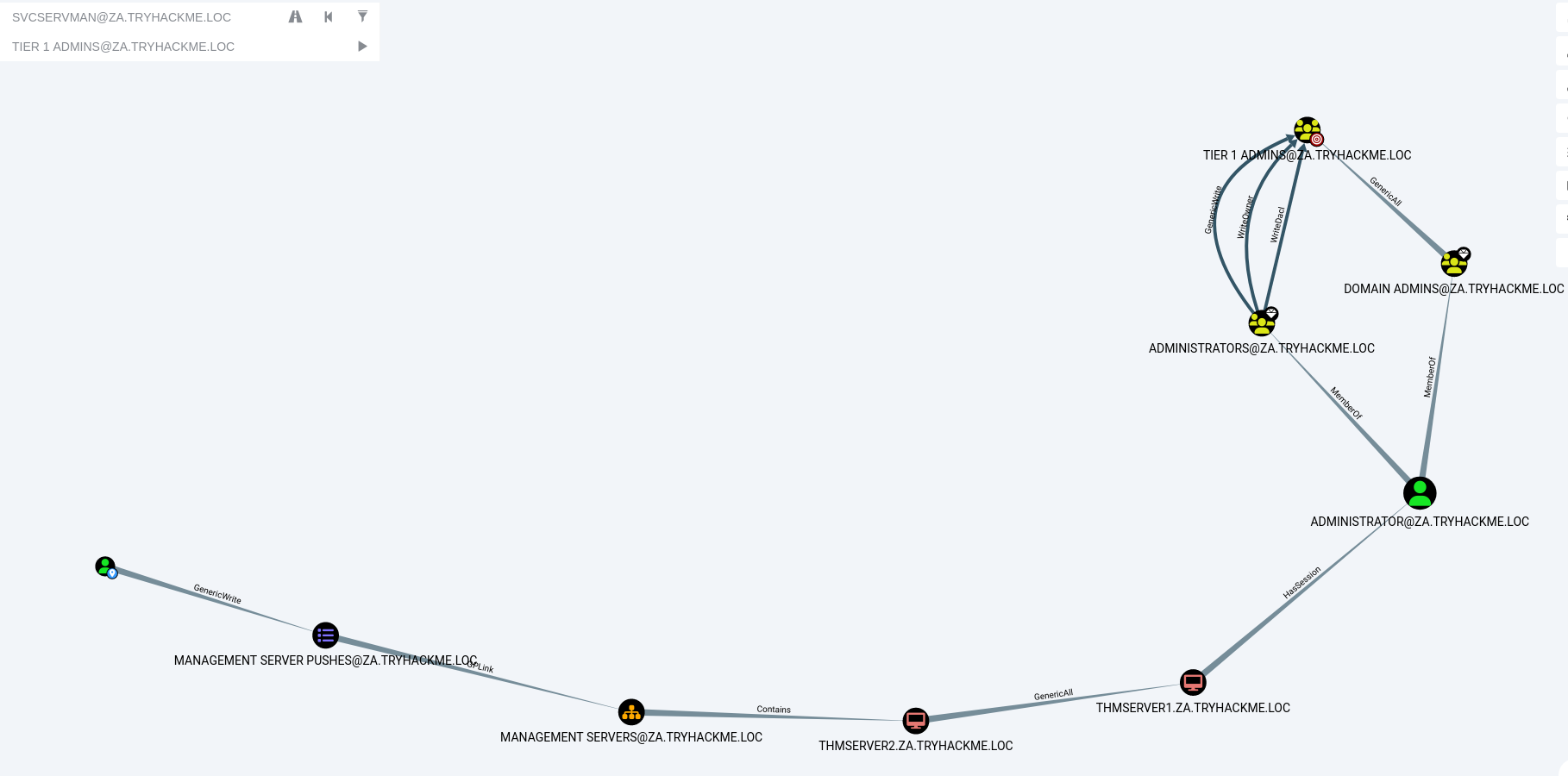
SVCSERVMAN -> Tier1 Admins
The predefined queries also allow for the identification of “Dangerous Rights for Domain Users” and “Users with Foreign Domain Group Membership.” The findings from these can be vital when trying to breach a different domain or execute privilege escalation.
Bloodhounds GUI can even aid in the enumeration of the network. With the environment mapped out, an attacker will be able to investigate groups, see which user has access to what machines, where user accounts have open connections and sessions and much more.
Blue-Team Perspective : Securing AD through the eyes of an attacker
As discussed in the Red Team section of this blog, Bloodhound can aid in the discovery and visualisation of misconfigured policies, groups with dangerous permissions, avenues of attack and can also reveal hidden connections between workstations and servers that may have been previously unknown.
Finding these misconfigurations will allow organisational defenders to investigate this within their domain and either resolve the potential attack avenue or come up with a workaround for the issue.
Depending on how long an organisation’s AD network has been active and if any security reviews have taken place, there could be thousands of attack paths that the security team want to resolve. Due to this, we suggest working from the top of the domain (highest privilege) down until the risk can be accepted.
Visualising the domain may also introduce a new way of thinking and configuration when it comes to the network. The security team may realise that they need to introduce tiered administrator groups to have tighter control of permissions and access.
The graph may also indicate that stricter permissions need to be added to larger groups/Organisational Units (OUs) – for example, every member in the Finance department has permission to RDP to a server running finance software when, in reality, only a few need access. While this isn’t a large security threat, it increases the surface area of the attack.
In 2023, 66% of organisations were affected by Ransomware (Report by Sophos). Bloodhound obviously cannot defend against ransomware. However, the visualisation can aid the security team in securing the network layout and determining if fringe servers can be isolated with stricter rules on communicating with internal servers and workstations.
The roadmap feature will also allow the blue team to investigate paths that can be taken to compromise higher privileged accounts. This can be beneficial, especially when trying to bolster the overall domain security. Road mapping to privileged accounts will identify any groups or users who have privileges over an account they shouldn’t.
The following image demonstrates how a regular domain user can gain control of the Tier 2 Administrator group within the TRYHACKME.LOC domain. On the far left of the image, you can see the domain user. A connection links this user to the IT SUPPORT group, labelled with the “Generic Write” role. This permission enables the domain user to modify information about members within the IT Support group, including the creation of new user accounts. Allowing the domain user to become a member of the group. Continuing to work left from right, BloodHound reveals that any member of the IT Support group has the ability to change the passwords of members in the T2 Admin group. By leveraging this privilege escalation, a domain user can use the newly created IT Support account to reset the password of a T2 Admin user. This allows the domain user to take control of the T2 Admin account, effectively granting them elevated administrative privileges.
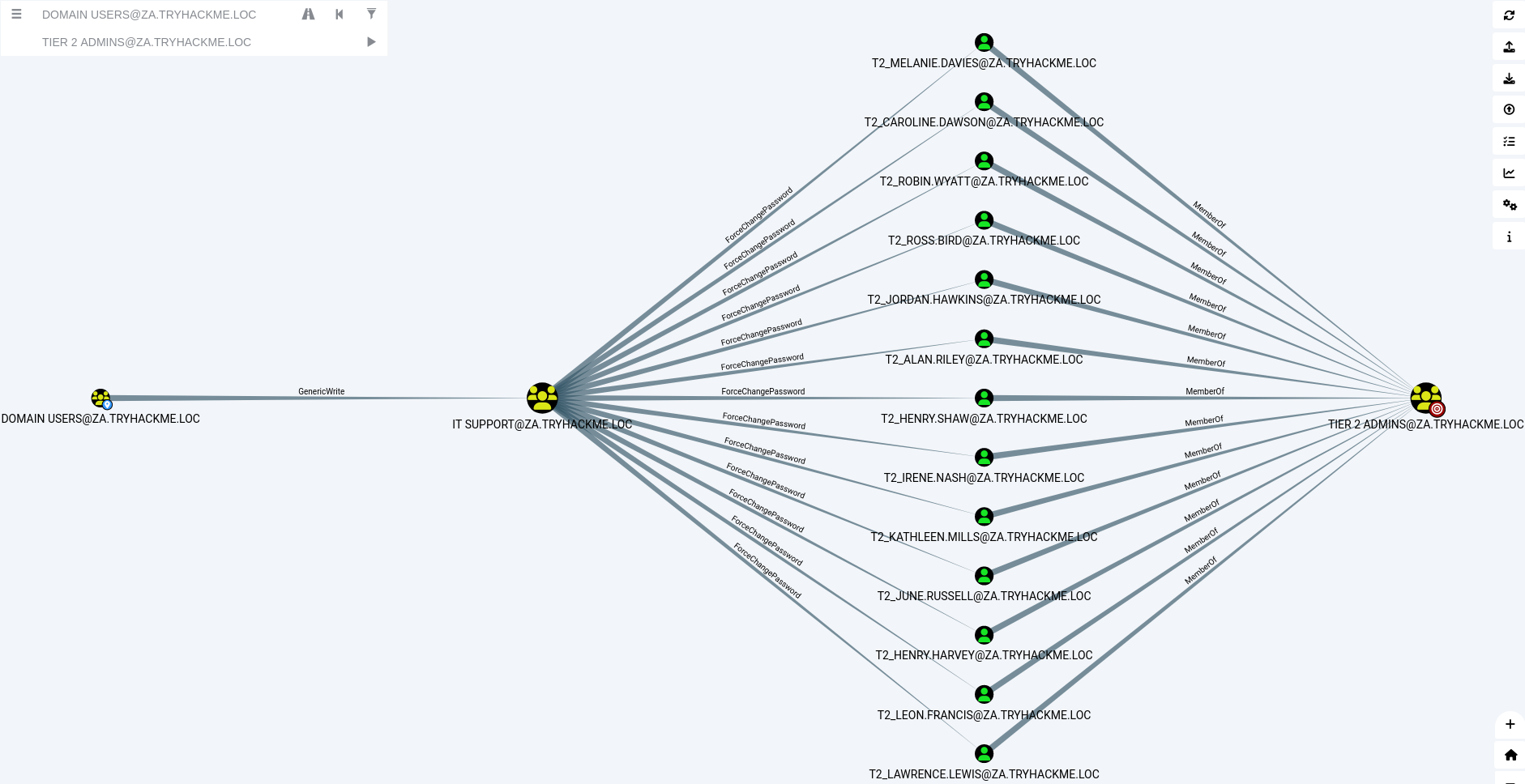
Domain users to Tier 2 admin roadmap
Performing weekly Bloodhound checks will also aid in awareness and overall security posture. If every Monday morning, the security team were to compare a recent AD graph to one from a previous week whilst also checking some queries relating to Administrator accounts, they could potentially spot signs of compromise or malicious activity regarding account creation/permission provision within the domain.
Comparing multiple Sharphound databases, the blue team will be able to visualise changes to group permissions and any users that have been added to user groups, even if an adversary has tried to hide them through obfuscation (Adding a user to a group within a group within a group etc…) and will aid in the continual improvement of the organisation’s overall security posture.
Bloodhound also has a built-in query that will return any workstation or server with an out-of-date Operating System. This is great when trying to identify a quick lay-of-the-land and working on which servers need to be upgraded and the criticality of these upgrades.
Bloodhound is also fantastic at identifying Kerberoastable user accounts (What is Kerberoasting?), and the built-in query “List all Kerberoastable Accounts” will display all accounts that are susceptible to the attack. If this query brings back too many accounts, I would suggest starting with “Find Kerberoastable Members of High-Value Groups”.
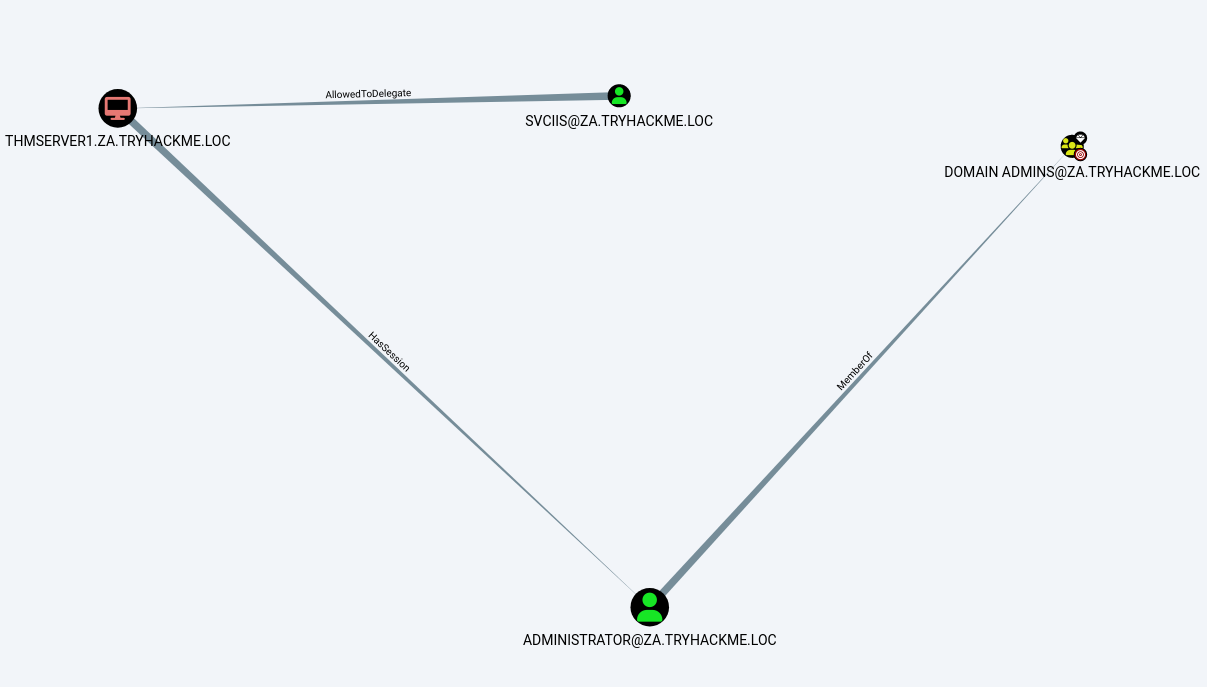
Shortest path to Domain Admins from Kerberoastable Users
Once these Kerberoastable accounts have been discovered, the security team will need to check account permissions and password complexities for the account. It is recommended that these accounts’ passwords are a random 64-character string that is rotated every 180 days, and it has the least amount of permissions applied whilst still letting the account complete its role.
Purple-teaming: Simulating Real-World Threats Using Bloodhound
Bloodhound provides a fantastic layout for performing a round-table purple-team assessment focusing on AD compromise. The visualisation of the network allows both teams to methodically work through attack vectors to theoretically determine which attacks would work and if any defences in place will either alert or block the activity.
The purple-team engagement also aids the blue team further in understanding exactly how an adversary would break down and digest the domain graph and plan their approach to the network, leaving the blue team better prepared if they were to use Bloodhound on their own in the future.
Hosting a round-table engagement will also allow the red team to launch attacks within the network to see if the defences work or if they need to be altered to cover a new area of compromise. It may also urge the blue team to create more alerts and implement more defences if the red team are completely successful.
As the red team will have the same information as a real adversary, they will be able to form realistic and organisational-specific attacks to measure the organisation’s defences.
Using Bloodhound for a purple-team engagement is very beneficial for the blue-team as it can aid in the identification of any misconfigurations, which will help them avoid similar misconfigurations in the future, increasing the organisation’s security posture in the long and short term.
Highlighting all the potential attack vectors and ways of compromise will also emphasise the importance of continuous monitoring and incident response to an organisation, potentially leading to an increase in budget for security tools and defences.
If an alert is triggered for an actual attack, the blue team will have a better knowledge of what workstations and servers they need to isolate to mitigate any further damage, increasing response time & effectiveness and allowing for the sanitisation of the environment to occur quicker.
Conclusion
Bloodhound is a great tool that has a wide range of uses on both sides of the cybersecurity spectrum. It is vital when enumerating a Domain on a red-team assessment as it cuts out the guesswork of escalation and movement and allows the attack to be precise and effective. This is also why it is so important for a blue team to implement it when reviewing their AD security posture. It can help in the identification and mitigation of attack vectors, misused accounts, groups with wrong permissions and overall network security topology.
As a red-teamer, Bloodhound can plot attack avenues, which can then be integrated with phishing campaigns to make for a swift, effective and brutal domain takeover. Bloodhound can also return interesting information about server Operating Systems, workstations that can RDP to other servers and highly privileged groups that may have desirable permissions. It allows the red team to create a plan of attack whilst being offline, leaving the blue team completely unaware of what’s going on.
Bloodhound is vital for a blue team as it provides an easy-to-digest and interactive way of looking at their network through an attacker’s eyes, highlighting all attack avenues and providing them with many findings that can be resolved to increase overall security posture. It can also help with future planning and creation of servers and OUs regarding isolation and permissions needed.
Using Bloodhound in a purple-team environment allows for defences to be tested and the blue-team to learn what they should be looking for and any extra defensive steps that are required. It also offers the red team the opportunity to provide input on the permissions of groups and users to try and get as close to the principle of least privilege as possible. Bloodhound allows for a free-flowing collaborative effort when conducting a purple-team assessment that cannot be matched by any other tool on the market.
Helpful Bloodhound Queries
Find Unsupported OSs:
MATCH (H:Computer) WHERE H.operatingsystem =~ ‘.*(2000|2003|2008|xp|vista|7|me)*.’ RETURN H
Find Servers a user can RDP into:
match p=(g:Group)-[:CanRDP]->(c:Computer) where g.objectid ENDS WITH ‘-513’ AND c.operatingsystem CONTAINS ‘Server’ return p
Find Workstations a user can RDP into:
match p=(g:Group)-[:CanRDP]->(c:Computer) where g.objectid ENDS WITH ‘-513’ AND NOT c.operatingsystem CONTAINS ‘Server’ return p
Find if unprivileged users have the right to add members to groups:
MATCH (n:User {admincount:False}) MATCH p=allShortestPaths((n)-[r:AddMember*1..]->(m:Group)) RETURN p
Many more useful and probing queries can be found here
How can Cyber Alchemy Help?
At Cyber Alchemy, we understand the critical importance of securing your Active Directory environment. Bloodhound is an invaluable tool for identifying and visualizing potential attack paths, but extracting actionable insights and configuring it for optimal use can be challenging. That’s where we come in.
Our team of seasoned cybersecurity experts specializes in leveraging Bloodhound to its fullest potential. We offer comprehensive reviews of Bloodhound findings, translating complex data into clear, actionable recommendations tailored to your unique security needs. Whether you’re a blue team looking to fortify your defences or a purple team aiming to enhance collaboration and incident response, Cyber Alchemy provides the expertise to guide you every step of the way.
Beyond analysis, we assist in the seamless configuration and integration of Bloodhound into your security operations. From initial setup to advanced query customization, we ensure that your blue team can effectively utilize Bloodhound’s capabilities to detect vulnerabilities, monitor anomalies, and continuously improve your security posture.
Your Business: Secured
Unique | Unmatched | Strategic
The best Cyber Security Company you’ve never heard of. Empower your cybersecurity with tailored solutions that address your unique challenges. Let’s make your operations resilient against emerging threats.
References & Further Reading
Install Guide – https://Bloodhound.readthedocs.io/en/latest/installation/linux.html
Github – https://github.com/BloodhoundAD/Bloodhound
THM – https://tryhackme.com/r/room/exploitingad
Sophos – https://assets.sophos.com/X24WTUEQ/at/c949g7693gsnjh9rb9gr8/sophos-state-of-ransomware-2023-wp.pdf
What is Kerberoasting – https://www.crowdstrike.com/cybersecurity-101/kerberoasting
Changing Kerberos Passwords – https://techcommunity.microsoft.com/t5/core-infrastructure-and-security/faqs-from-the-field-on-krbtgt-reset/ba-p/2367838
Changing Kerberos Passwords – https://blog.quest.com/what-is-krbtgt-and-why-should-you-change-the-password/
Bloodhound CheatSheet – https://hausec.com/2019/09/09/bloodhound-cypher-cheatsheet/